As someone with a daughter who rides horses I have often been asked – “how can you own something that eats while you sleep?” This led me to thinking about ERP and how your ERP software can “think” while you sleep or at the very least provide an additional “eye” on running your business.
You might be asking yourself – what exactly does she mean? Imagine these scenarios, if your system could let you know:
- when someone is trying to access a functional area they do not work in;
- if your system administrator inadvertently tried to run two month ends in succession;
- if an operator managed to approve a purchase for a value above their approved limit;
- if a valued customer had reached 80% of their credit limit and the system was about to prevent them from purchasing.
Managing and monitoring these risk areas can consume both executive time and energy when in fact your system should be set up to generate alerts and enable you to get on with running your business knowing the risks are taken care of.
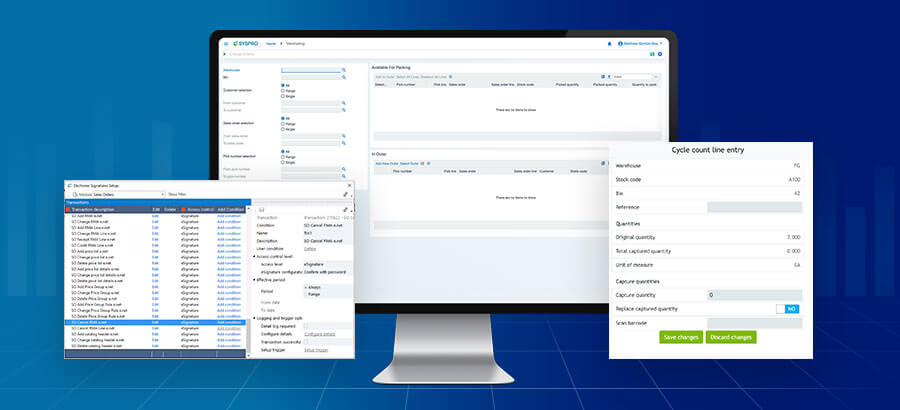
Most good ERP products should contain configurable Alerts, Triggers and Events that you can personalize to either prevent the action, send an e-mail notification to a predefined person, or output information to a log for later analysis.
I was recently speaking to a friend who runs a large organization and some of her key people had defrauded the company of a large sum of money. Even the auditors who had recently done an audit and signed off the books did not pick it up. In analyzing the situation this was possible as they had no clearly defined processes, they had not applied role segregation and there were no underlying triggers to either prevent actions or send notifications. So how could this have been prevented?
- The company should define and document, in detail, their full processes for buying, selling, manufacturing and administering their company. This documentation should include roles and departments responsible for performing each step in the process. In addition risk areas need to be identified and noted on the process documentation.
- Once these processes are documented they should be signed off by two or three senior executives in the organization. In signing off the processes a check should be done to verify the Role segregation.
- A copy of the processes should be made available to the auditors for verifying when they audit the books. The system should allow for the operator/role performing each function to automatically be recorded against the journal and be visible in the general ledger.
- The system should be set up with the correct security in place to facilitate role segregation.
- The system tools for trapping Alerts, Triggers and Events should be configured to ensure the risk areas have been trapped and appropriate actions configured, so the correct access prevention, notifications or logs are actioned.
Spending the time and energy in getting the above correctly set up and configured for you and your organization will bring peace of mind and assurance that you have done whatever you could to mitigate risk. Nothing wrong with letting “your system work while you sleep”…