The digital pandemic is upon us. Over the past few months, a number of critical businesses have faced cyber-attacks. Earlier this year, hackers infiltrated the Colonial Pipeline and demanded $4 million in ransom. While the ransom was paid on the same day, the pipeline was only able to function again after six days. A class action lawsuit is now seeking damages for costs and lost profits incurred by gas stations, that suffered losses in excess of $5 million.
Another sophisticated ransomware attack recently targeted the world’s largest meat processor. The business-system breach led to the shutdown of multiple plants in the US and Australia. Several truck drivers who specialize in hauling livestock also had no choice but to drive hundreds of miles to pick up cattle from an alternative supplier. For the end-consumer, the long-term impact of the cyber-attack could mean inflated meat prices.
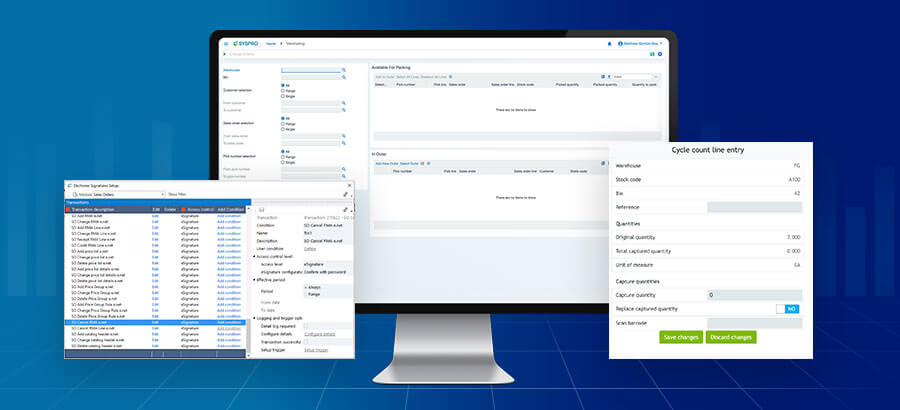
With increased reliance on digital tools, businesses are now understanding the importance of company-wide cybersecurity strategies that take into consideration all IT systems. For manufacturers and distributors, this includes your Enterprise Resource Planning (ERP) solution, as it integrates internal systems and integrates with external third-party systems.
ERP systems contain sensitive information ranging from supplier information on the creditor side and customer information on the debtor side. From a compliance perspective, this information needs to be carefully protected. There is no doubt that ERP is at the heart of the business and needs to be an integral part of the cybersecurity strategy of the organization.
Here are the steps a business should take to safeguard your ERP system.
Step 1: Recognize the usual suspects
It is vital for businesses to watch out for specific ‘social engineered’ scams. The most common attack on ERP systems are Distributed denial-of-service (DDoS) attacks. Here cybercriminals target a public-facing endpoint, where a network resource is rendered unavailable to intended users. One of the most infamous DDoS attacks was launched back in 2000. The culprit? A 15-year-old ,with ‘Mafiaboy’ as his online alias. The teenager carried out the attack by hacking into the computer networks of a number of universities and used their servers to crash a number of high-profile websites including CNN, E-Trade and Yahoo.
Broadly speaking, phishing is another example where criminals can exploit systems by sending emails that seem to be from trusted sources or companies. For example, an ERP customer would receive an email from their ERP vendor, often promising a reward or refund, to deceitfully obtain personal information, including passwords, identity number, banking login details.
Another example is pharming. Pharming is a cyber-attack intended to redirect a website’s traffic to another, a fake site that aims to steal your information. In a pharming attack, the criminal hacks into the website you have opened and redirects you to an imposter site. Much like a phishing scam, many of us won’t notice any difference in the rogue site and will enter your username and password, or credit information as usual. The attacker then intercepts the captured information.
All of these attacks lead to one common denominator – the human factor. Your staff need to be reminded not to open suspect emails, be wary of unexpected messages, and be reminded to change their passwords often.
Step 2: Always update your software
Software is continuously evolving – and this includes your security software. It is reported that 87 percent of business computers have outdated software, including ERP systems which are not up-to-date. If your version is currently unsupported, it can make it difficult to rectify any security weaknesses. Businesses therefore need to always install the latest versions of any software to remove any vulnerabilities.
Step 3: Access rights and correct role allocation are key
How often are all employees given full access rights to all data within the organization? Full access rights shouldn’t come as default; instead, it’s important to look at who has access to what data. This default access rights is a scenario that is ideal for cybercriminals as they seek sensitive information! You should instead ensure that employees are provided with specific roles and form part of groups with associated security and clearance authorizations.
Step 4: Always use a multi-factor authentication approach
Back in the day, one-factor authentication was enough, but it is now archaic.
Instead, businesses today need to have an extra layer of security with two-factor or multi-factor authentication.
Cybercrime threats has definitely become more prevalent as the world made a shift to remote work. Because the human factor can place your business at risk, a rinse and repeat approach should be taken around cybersecurity education.
It’s now up to businesses to remain vigilant and take the necessary steps to protect their ERP solutions from malicious intent